What data is transferred by business apps and how secure is their processing? Our research shows: If your employees use apps arbitrarily, you put your company’s security at risk.
At it-sa 2022, we present our app analysis framework Appicaptor, which you can use to automatically check whether apps are compliant with your company’s IT security demands. New, within the BMBF funded research project PANDERAM developed methods will complement Appicaptor. Among other things, the goal is to identify, evaluate and visualize complex data flows from automated dynamic analyses.
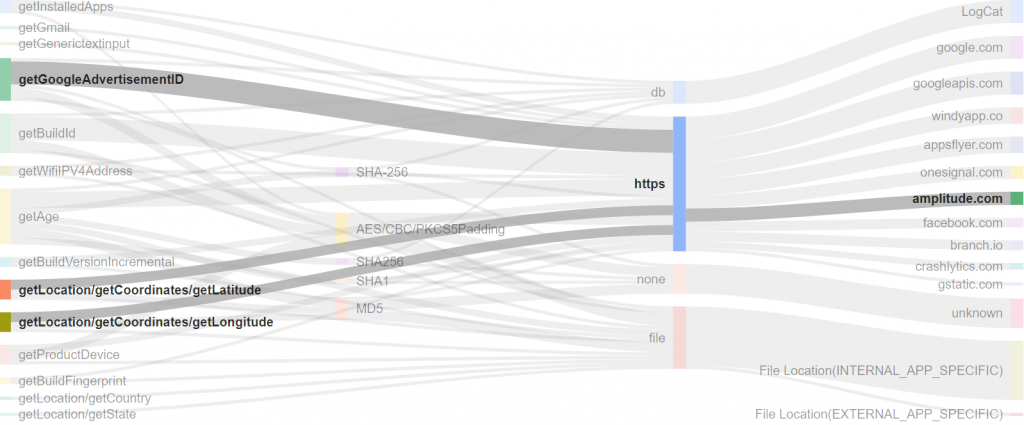
One focus of the ongoing PANDERAM project is to develop an analysis platform using a lightweight approach for automatic data collection from large app sets in order to provide users with information about the IT security quality and privacy of their apps. The technical basis is built upon dynamic analysis of app security properties by applying hooking techniques within a custom-built runtime environment.
Using this approach, the IT security quality of apps is automatically evaluated, including issues that go beyond the aspects observable at communication level such as lack of encryption in local data storage or usage of weak cryptography. By hooking system functions, the evaluation environment also detects access to system resources such as memory card, calendar, contacts, etc. The dynamic approach allows TLS pinning to be switched off, so that transmitted data can be read and evaluated depending on their triggering factors. Furthermore, the analysis platform includes unsupervised operation and usage of apps, which autonomously recognizes specific app operation concepts for the analysis of a large functional scope of apps. Particularly important here are approaches for dealing with login fields, recognition of navigation elements and other interactive elements that must be correctly recognized and operated at app startup in order to enable app functionality.
The example of an Android weather app above shows a first visualization of the analyzed data flows. Highlighted are the location and advertisementID information that are transmitted to third parties when the app is granted the required permissions. For weather apps the example demonstrates the problem, that the user wants to share the location to retrieve the local weather. However, all included third-party libraries get the permission to access and transmit the location information for their purposes as well. Which might not be in the interest of the information owner. Fraunhofer SIT’s Appicaptor specific data flow analysis methods will evaluate the transition of corporate or business data to external parties on that concept.
You’ll find us in hall 6, booth number 6-210 for a demonstration.
