The use of apps in enterprises requires a critical consideration of the included risks in order to be able to effectively counteract the threats through an analysis and approval mechanism. Today, we have published results of automated Appicaptor analyses for the top 2,000 free iOS and Android apps.
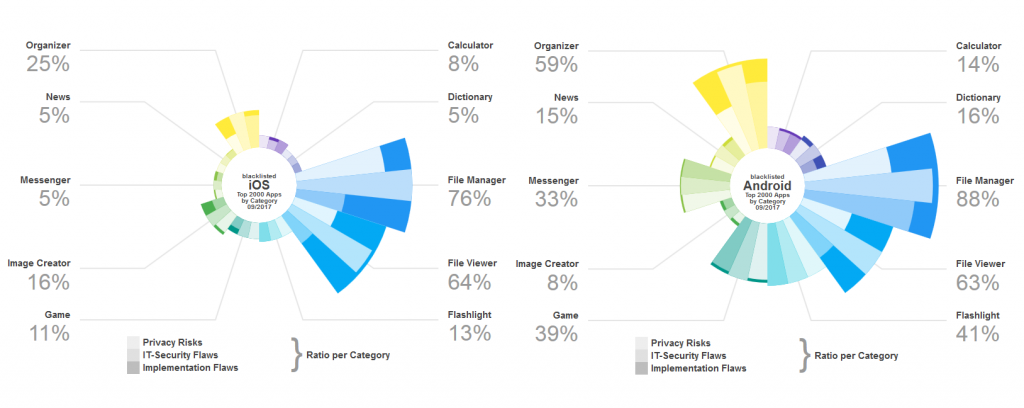
When assessing the fitness for corporate use, it is not very surprising that apps for the processing of corporate data are quite critical. In particular, the functional class of the File Manager apps shows a significant risk of usage with 76% iOS apps classified as unsuitable for corporate use (see figure). This is even higher with Android at 88%. The reasons for the blacklisting of both platforms are a very high ratio of IT security weaknesses and privacy relevant risks (see report for further analysis details).
The report also shows new insights about security characteristics of hybrid apps, which affect resources such as the phone book, calendar, clipboard, position data and even access to local data storage in the sandbox of the vulnerable app. For the ratio of analyzed Cordova iOS apps, 81.6% (Android 80.3%) currently have the precondition for manipulating the app via web content to attack the JavaScript bridge to smartphone resources.
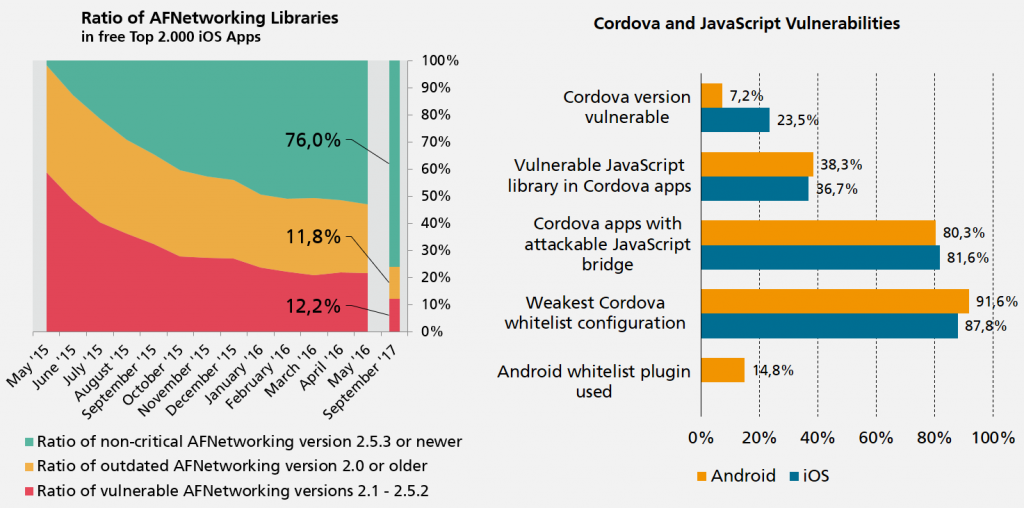
The effects vary greatly depending on the smartphone resources used and the data processed. However, the ability to include these factors in a code analysis automatically allows for a more accurate risk assessment, so that only those apps that pose a specific risk are excluded from use in the company.
Other risks for Cordova apps are also the use of known vulnerable Cordova versions, which are used by 23.5% of iOS and 7.2% of Android Cordova apps. This makes it possible for attackers, e.g. under Android in Cordova versions prior to 3.5.1 to launch the Cordova app with other HTML page content via a link in order to misuse the available plug-ins with access to critical resources for their purposes.
But also the ratio of known vulnerable JavaScript libraries in Cordova Apps is a major problem with 36.7% (Android 38.3%). For example, using the vulnerable Angular. js version 1.4.4 allows attackers to break out of a secure ng-bind-html environment by manipulating user input. This environment normally allows only HTML formatting to be used, calls of JavaScript or other active content are prevented. The known weakness of this version allows attackers to bypass the protection mechanism, which again allows all available permissions of the app to be abused by an attacker.
Download the complete Appicaptor Security Index 2017.
