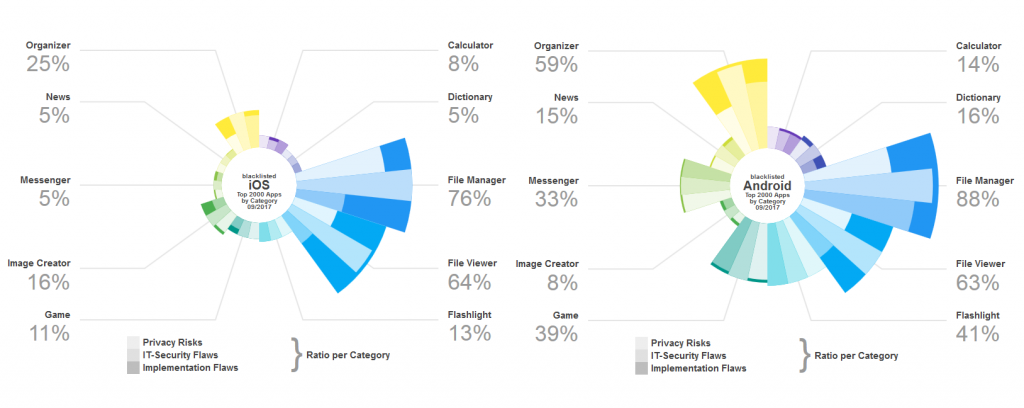
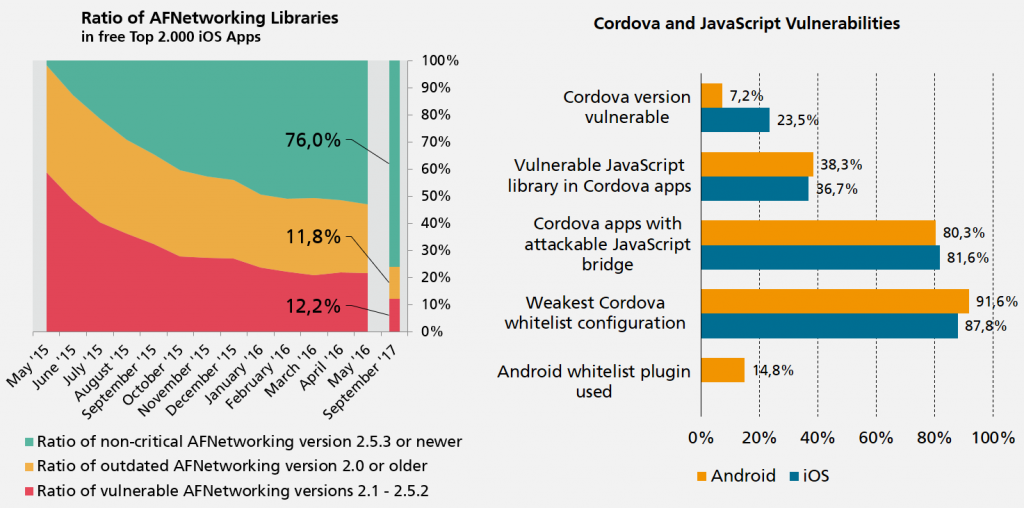
The BankBot Trojan is back in the news, targeting German mobile banking apps as well. While most articles ask how this Trojan could bypass Googles reviews and Google Play Protect on-device checks, we miss a consideration of protection measures implemented by mobile banking apps.
Before looking at the app protection side, one has to consider that this Trojan requires three critical Android OS settings to be configured: the smartphone user (1) has to opt-in for app sideloading, (2) has to acknowledge the installation of an additional component and (3) has to grant the device administration permission to the Trojan. However, in more advanced attacks these settings could have been configured even without notice of the user, as found in the TOASTAMIGO malware. After applying these settings, the Trojan has critical privileges, but is far away from the dreaded root privileges. Chances are still good that app protection mechanisms would make it harder to successfully perform an unauthorized transfer.
From a banking app developer’s point of view, a first line of defense would be to implement a so called tapjacking protection. This way, the Trojan would not be able to redirect touch events of a crafted overlay to the exported activity of the mobile banking app below the overlay.
However, only 5.2% of the analyzed Android banking apps currently have implemented this protection (Appicaptor Top 2000 Report, November 2017). Even worse, about 67.4% still contain unencrypted HTTP requests (btw: redirecting these requests on server side to HTTPS is by far no effective protection). These requests commonly are not used for the main banking interaction functionality but often are found for additional services, such as address finders or terms of conditions pages. Unencrypted HTTP communication could be abused in the trusted bank app context for dangerous phishing attacks.
The effort for implementing proper tapjacking protection and removing HTTP requests within the mobile banking app is quite low compared to the obtained improved security gain. But these measures would not prevent Trojans from displaying a fake UI over the real one of the mobile banking app, like the BankBot Trojan does. We already have committed a security patch to the Android Souce Code repositories in order to stop tapjacking attacks on the Admin Device Permission Request window, however this does not prevent more sophisticated attacks exploiting “Toast type” overlays. The latter overlay attacks are fixed with Android’s security patch level of 2017-09-05. Additional improvements are integrated in Android 8 Oreo, which prevent apps from overlaying the smartphone’s status bar and display a persistent notification about apps running in the background. However, there are already apps in Google Play Store, which offer the option to remove these “annoying App X in background notifications”. Trojans would also be able to hide “their” app in background notification, too.
This shows that the Android OS and its app environment is not ready for combining separated banking channels: the transaction and the authorization channel. This separation was introduced for good reasons, but the current trend for mobile banking apps indicate a strong demand for using both channels on a single device. However, the observed security quality of current mobile banking apps does not reflect the required protection level for the introduced risks.