Well, no big surprise but still another investigation on the topic how developers deal with the password problem: A scan of 1.8 million Android Apps revealed 20,000 apps with insecure keys built in, such as PGP keys, VPN access codes and hardcoded admin passwords.
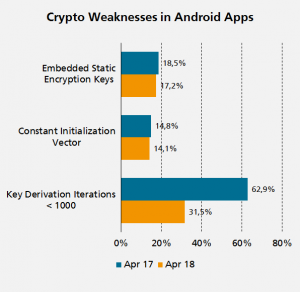
Embedded static encryption keys in apps were also identified by Appicaptor in 17.2% of the Top 2000 Android Apps in April 2018. Those keys can be extracted by attackers to target the security mechanism it is used for, e.g., to revert the utilized encryption or fake content signatures.
Constant initialization vectors for encryption mechanisms, which allows an attacker to infer relationships between segments of encrypted messages with the same key and initialization vector, were identified in 14.1% of those apps.
A third weakness regularly found are low numbers of applied iteration rounds within key derivation functions. A key derivation function (or KDF) derives one or more secret keys from a secret value such as a master key, a password, or a passphrase using a pseudorandom function. So, the difficulty of a brute force attack increases with the number of iterations the KDF is executed, which should be at least 1,000. However, 31.5% of the most popular Android apps still use fewer iterations.
The good news is a positive trend for these weaknesses for the last years, but the total number of the found weaknesses does not indicate that the correct handling of cryptographic secrets and key derivation is already thoroughly understood from app developers (even at widely applied apps such as the Android Top Apps).
